Hello Friends !
while trying my luck with Uber i came a cross a wired behaviors in the application which is not very common in today’s world.
i was messing around with password reset token generation of Uber, while requesting for password reset link i appended some known get parameter with password reset request which i was noticed before while checking for URL redirect issues in there oauth implementation.
it was NEXT parameter which is responsible for next URL or page after successful login.
so now come to password reset page, normally Uber password reset page URL looks like : https://login.uber.com/forgot-password , where crafted URL looks like : https://login.uber.com/forgot-password?source=auth&next_url=evil.com .
so once users will request password reset token via crafted link , user will get password reset token and once user set his new password, user will redirected to evil.com.
its a bug but as we know Uber don’t accept URL redirect issue until and unless there is something special, as URL redirect take place while password reset, i need to take advantage of it.
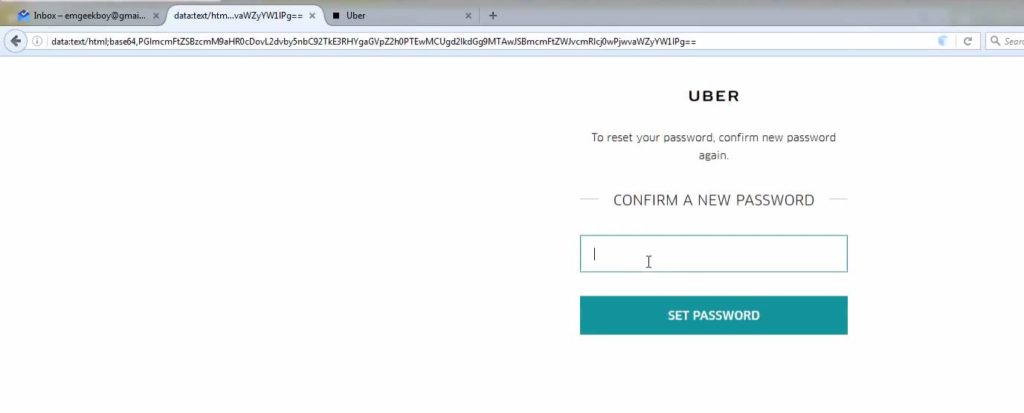
i made a form which looks like same as Uber form which ask for Confirm Password after user sets his New Password which looks like :
i used data: scheme to make sure it looks more legit instead of using any direct URL.
so now the scenario is :
- Attacker will request password reset token via crafted Link.
- Let’s assume user reset his password via reset link.
- User will set & confirm the new password.
- Attacker will get users new password.
as we can see its not win-win case , still we need to depend on the user if he choose to reset his account or not, but still it may happens and in that situation attacker will get password of users account, so Uber decided to fix it once i reported , and they were very quick to acknowledge the report, i will suggest to participate in Uber bug bounty program .
Here is the Video POC :

good one! great job bro!
Nice one 😉